 Challenges
Challenges
Enterprises are increasingly relying on the Internet to process business, and the risks of Internet access are becoming more and more severe. In addition, the WAN uses various networking methods, and the business access relationship is more complicated, which brings more challenges to enterprise network security protection.
Therefore, enterprises urgently need to cooperate with their own network upgrade and transformation, improve the construction of network security protection system, strengthen network boundary protection, increase network defense depth, improve network structure security, and improve operation and management efficiency.
 Solutions
Solutions
G3S network security solutions focus on building management, technology, and operation, which helps the enterprise meet the challenge of digital transformation.
1. Network security management system
• Design rules and regulations for the network security management system.
• Give suggestions to enterprises based on the scale of network security construction and the evaluation result of the configuration of network security positions.
• Interview with departments, align the information security management with the business and ensure the promotion of the information security management system within the company.
• Refine the security management rules, and proceed from the corporate culture and development strategy, so that the rules can become a powerful driving force for the network security.
• Conduct information security training and network security training for enterprise employees regularly.
2. Network security technology protection system
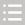
(1)Design of the network security structure
According to the function and security level, the network is divided into grids and regions, the scattered network boundaries are integrated, centralized management is strengthened, and a management network with physical or logical isolation is constructed to separate the management plane from the data plane, eliminate mutual influence, and ensure network management reachability.
(2)Build a defense-in-depth system
Build an enterprise-level network defense-in-depth system that fully covers all structural levels of the network, including the headquarters center, intranet access area, intranet aggregation area, regional center, branch nodes, partner access area, Internet access area, and Internet exit Access area, mobile office access area, public cloud access area, IoT access area, etc.
(3)Capability standardization and modularization
Using a standardized and modular network security protection cluster, the capabilities cover network traffic cleaning, network access control, traffic encryption and decryption, network intrusion prevention, network malicious code prevention, application security protection, security proxy, data leakage detection, and full-traffic network threat detection , attack trapping, etc., and the ability to flexibly configure and deploy clusters according to the business connection mode of each network node.
(4)Integrated management of security capabilities
Unified management of the security capabilities of all nodes in the entire network, implementation of dynamic and fine-grained network operation and maintenance privileged access control, global network data support, and automated and efficient management of security policies.
3. Network security operation system
• Determine operator organization, responsibilities, and design standard operating procedures and operational metrics
• Regular penetration testing of core business systems
• Conduct regular risk assessments of the overall network
• Conduct simulated drills of safety contingency plans regularly
• Code audits can be prioritized when new systems come online
• Carry out overall risk assessment for new construction and reconstruction of IT networks
 Advantages
Advantages
The solution systematically solves the security risks faced by the enterprise network, covering the construction of the network security management system in the early stage, the construction of the network security protection system in the middle stage, and the construction of the network security operation system in the later stage. The solution starts with the security of the network structure, eliminates the isolated island of security information through necessary security equipment and services, and forms a coordinated protection system to make enterprise security management more efficient.
 Introduction
Introduction


 Challenges
Challenges Solutions
Solutions
 Customer value
Customer value



 Advantages
Advantages





